Receive Sensitive Data Securely
Create One-Time Secure Upload Links
The Professional (and fully branded) Way to Receive Sensitive Data
How It Works
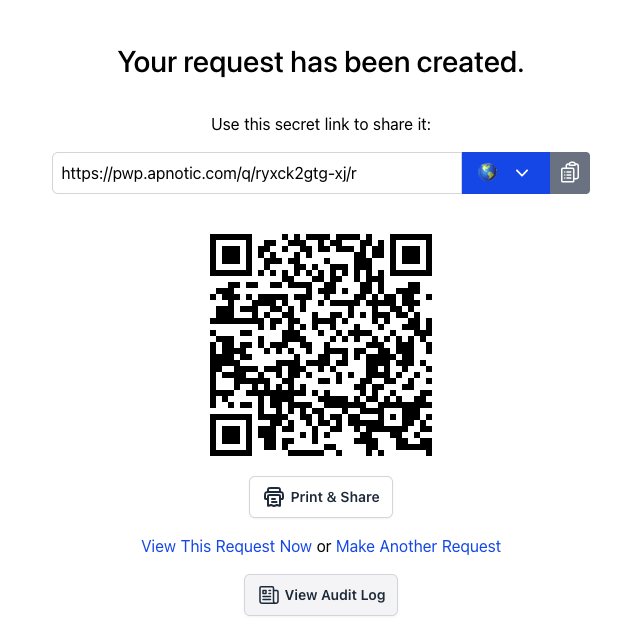
1. Create a request and a unique and hard to guess URL will be generated which can be shared with the recipient.
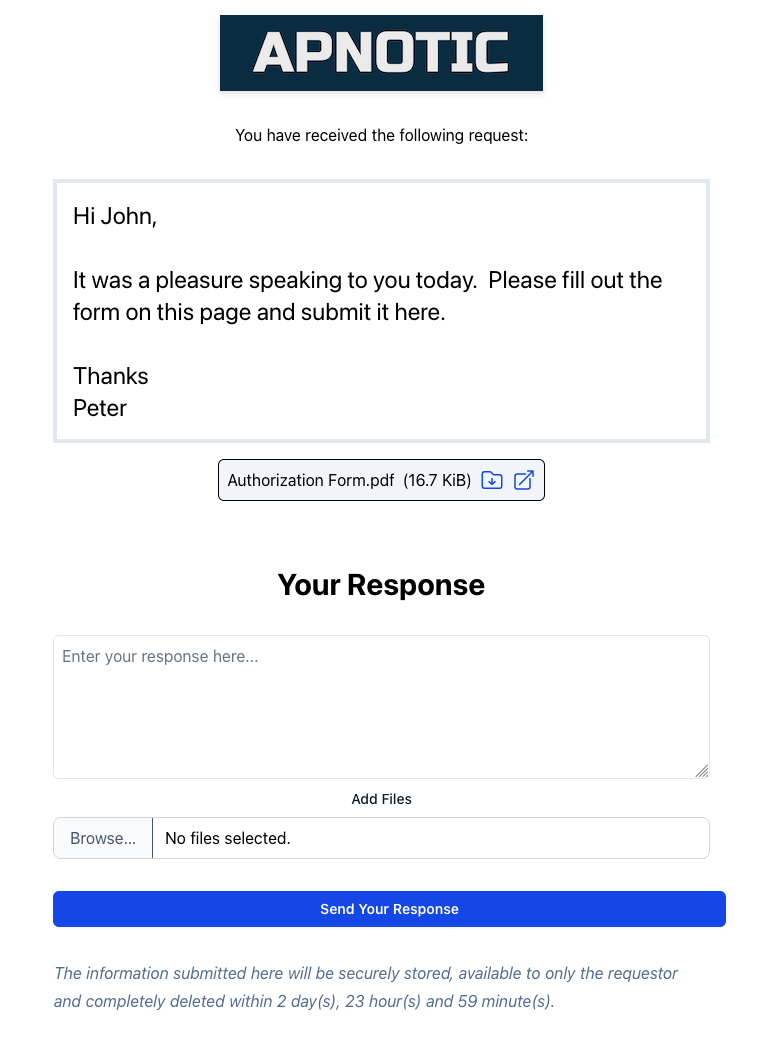
2. The person receiving this URL can view your request and respond with text and/or files.
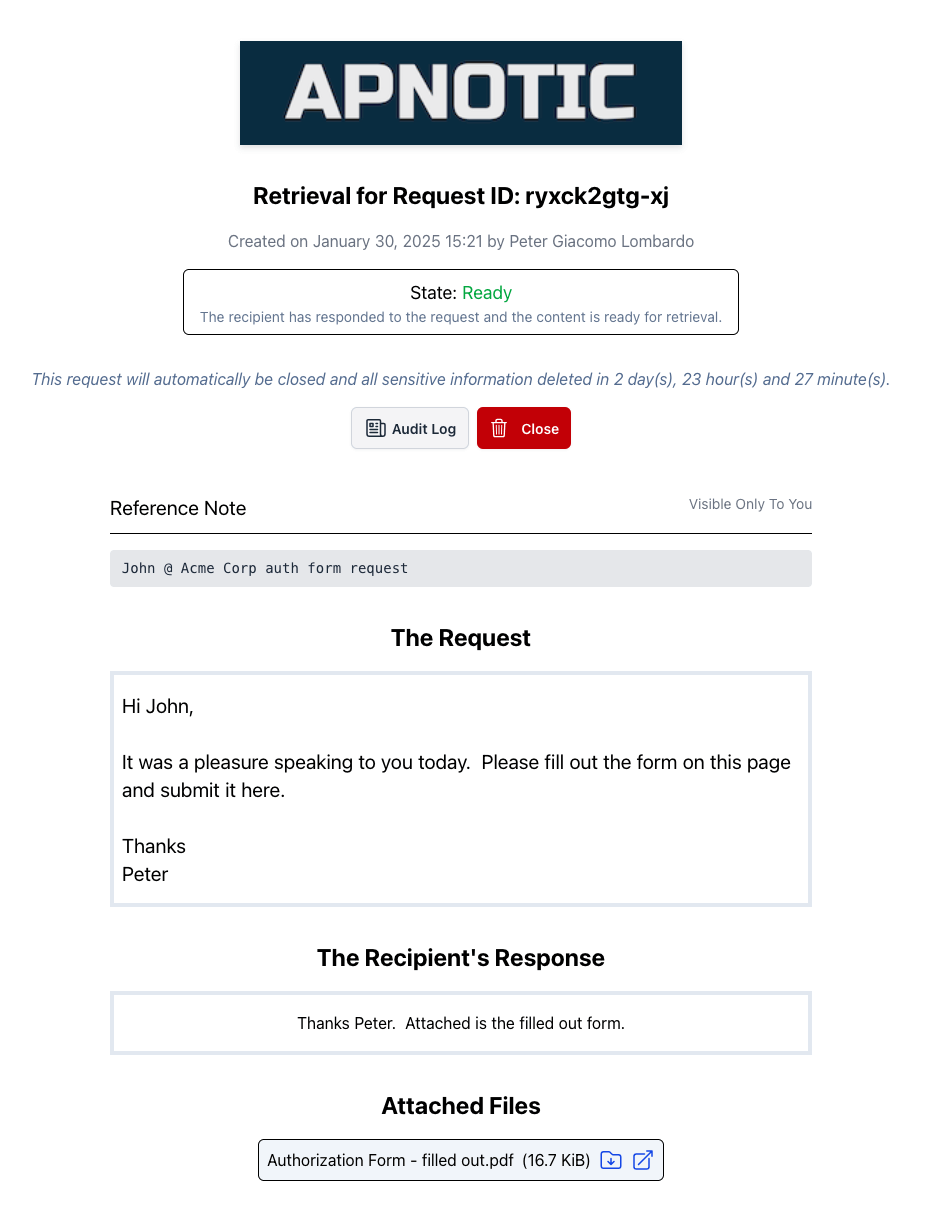
3. Once a response is received, you get a notification and can retrieve the response.
4. After the configured expiration, all sensitive data is deleted entirely.
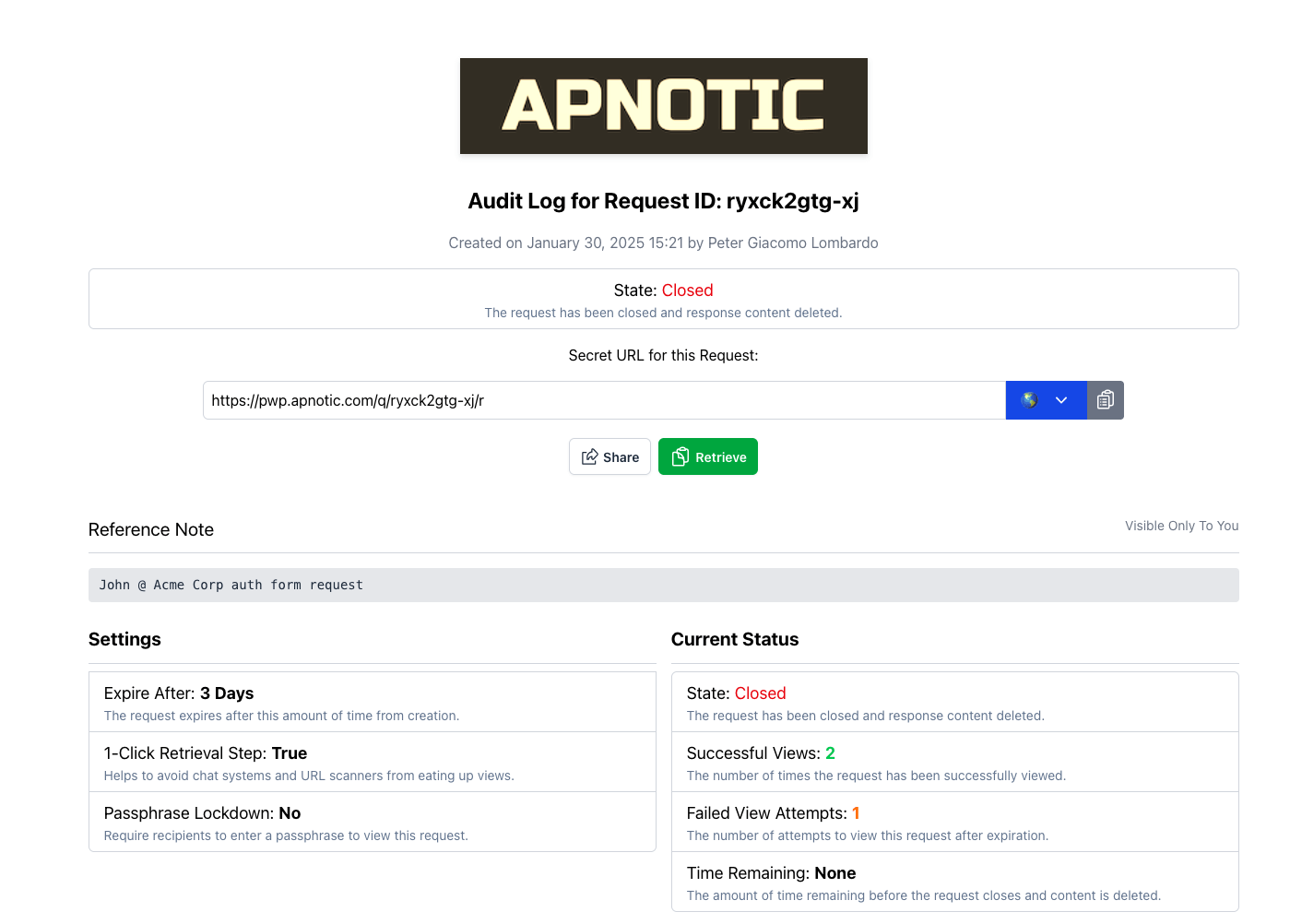
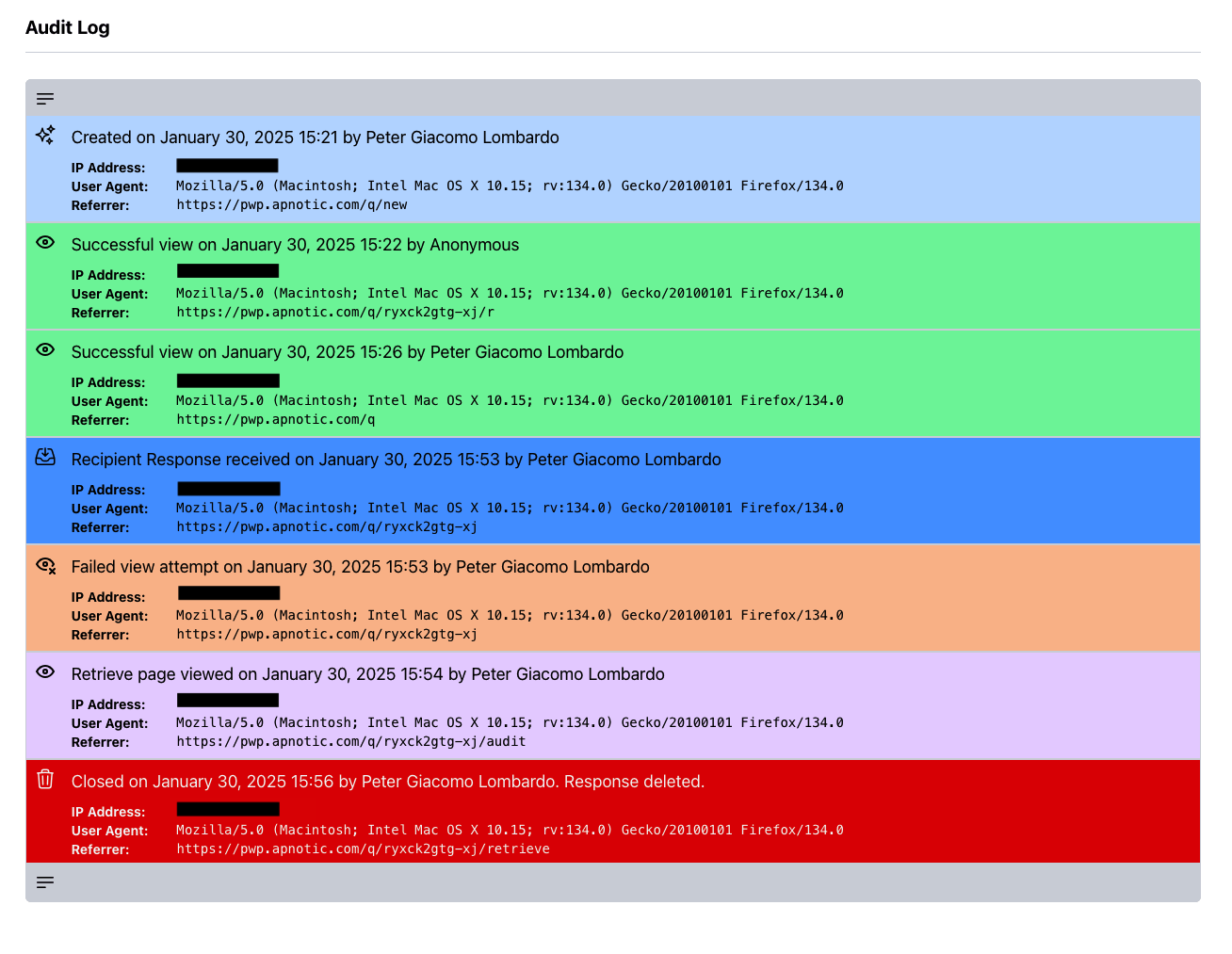
5. All activities related to your request are logged and accessible indefinitely to you and your team.
Benefits of using Password Pusher Requests
Data encryption, secure transmission and time-based expiration minimize the risk of potential breaches.
Track entire lifecycle of the request with permanent audit logs for you and your team.
All sensitive data is automatically deleted after expiration.
Customize the entire application with your own branding and text as a subscriber.
Protect your request with a passphrase to prevent unauthorized access.
Weave requests into your ticketing system and other tools.
Share requests with your team to collaborate on sensitive data.
* Read more about Password Pusher Requests here.
** Enable file attachments with a paid subscription.
*** Transmit and receive files up to 4GB in size.